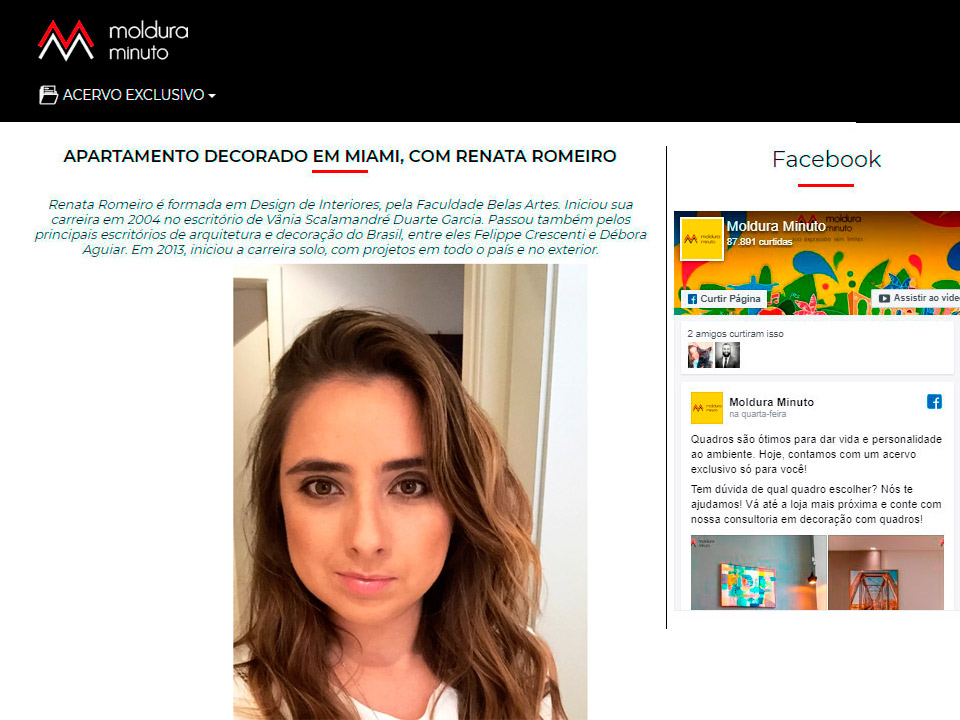
jump server architecture
Furthermore, the server continues to listen to client requests. A jump server is a hardened and monitored device that spans two dissimilar security zones and provides a controlled means of access between them. Software Architecture: One-Tier, Two-Tier The idea was simple: Designate one server as the control point and force users to log into that system first. Only the front-end is installed in the user’s PC not the application/database servers. Its architecture is optimized for security, portability, and scalability (including load-balancing), making it suitable for large deployments. Before we move on to Azure Bastion, let’s first understand what a Jump Box or Jump Host is. Jump to ↵ No suggested jump to results ... henningw changed the title module keepalive bug report keepalive module in two server architecture Feb 16, 2022. HPE Superdome Flex Server Architecture and RAS technical white paper. How Ansible Works We don’t recommend this approach because it’s not safer than the best practice achieved by modern PAM. It’s called front-end. The Client–server pattern Name Client-server Description In a client–server architecture, the functionality of the system is organized into services, with each service delivered from a separate server. It bridges two dissimilar security zones and offers controlled access between them. The chief benefit of three-tier architecture is that because each tier runs on its own infrastructure, each tier can be developed simultaneously by a separate development team, and can be updated or scaled as needed without impacting the other tiers. Internet access within the secure zone is restricted. architecture Then, by using this VM, we can connect to the other Azure VM’s using dynamic IP. Designing a network architecture based on security zones is an extremely effective method of restricting an adversary’s ability to move laterally within a network and gain access to administrative resources. X uses a client–server model.An X server program runs on a computer with a graphical display and communicates with various client programs.The X server acts as a go-between for the user and the client programs, accepting requests on TCP port 6000 for graphical output (windows) from the client programs and displaying them to the user (display), and receiving user input (keyboard, … In theory, cloud bursting is an ideal response to a spike in demand. Info: What is a Jump Server? - Venafi Customer Support Configure the Jump Server Settings for Privileged Identity Remote server system name: The actual name of the jump server. It talks to various device drivers that are running on PC's connected to the actual devices that are accessible within the work cell. Refactoring to microservices allowed Netflix to overcome its scaling challenges and service outages. Update: To help protect their assets, many security-conscious enterprises require their system administrators to go through a “bastion” (or “jump”) host to gain administrative access to backend systems in protected or sensitive network segments. Join our Discord Server. Permission: Manage server or Bot commander role. Clients are users of these services and access servers to make use of them. This architecture is used in a client-server application such as a web application that has the frontend, the backend and the database. SQL Server is not supported on ARM architecture. For installing the SQL database engine on ARM64, you need to use Azure SQL Database Edge. a. always is a two-tier network architecture. Product icons . A highly available architecture that spans two Availability Zones. Invite Link That means … Raspberry Pi 4 - Windows Server 2019 VMware ESXi 7. Azure Virtual Network. Jump box can be set-up easily using ARM b. always is an n-tiered architecture. 1. Try to use direct lines (rather than ‘criss-cross’), use adequate whitespace, and remember to label all icons. Client-server pattern. Consider a network with database servers, application servers, an HSM or NAE for PCI, and monitoring systems. But it also means that any user can access the server resources through the browser. This should be the name (FQDN, simple name, or IP) that can be reached from the client systems initiating the sessions. Client-server model is a distributed application structure that partitions tasks or workloads between the providers of a resource or service, called servers, and service requesters, called clients. One great way to … It is usually security hardened and treated as the single entryway to a server group from within your security zone, or inside the overall network. Hello everybody, I am upgrading Splunk Enterprise from 7.3.X to 8.2.5 (Windows). Copy link Member miconda commented Mar 4, 2022. Secret Server’s architecture can be adapted to include jump host functionality if the situation warrants it. One of the best choices for a small business is a dedicated server built from the ground up as a file server to provide features and expansion options that a desktop computer lacks. In part three, we looked at network security at the subnet level. This completes processing on the server side. Through SAP GUI. A cloud bursting architecture is a jump too far for many businesses. To add a new server, click Add. A jump server, jump host or jump box is a system on a network used to access and manage devices in a separate security zone. Bastion hosts, NAT instances, and VPC peering can help you secure your AWS infrastructure. Server: This application sits on the main work cell PC. Before we jump into solving Emma’s problems, let’s quickly define what SMP and MPP are. Deployment Server is a dedicated server that has to have the standard Splunk stand alone server: 12 CPUs, 12 GB RAM, 100 GB disk, virtual server. Usage A server-streaming RPC is similar to a unary RPC, except that the server returns a stream of messages in response to a client’s request. Bastion Host | Jump Server Bastion hosts are instances that sit within your public subnet and are typically accessed using SSH (for Linux) or RDP (for Windows). c. places all or almost all of the application logic on the client. GUIDE TO GENERAL SERVER SECURITY Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare … Broad Street is a server for drug OwO bot primary commands are the ones regarding animals, which you can hunt down, sell Use the tool below and you can buy some! ... BeyondCorp architecture reference from Google. This last one in the list is actually a huge poster that includes all of the other items, which are mini-posters describing a specific function. A jump server is an intermediary server through which external agents, such as the Venafi Trust Protection Platform (TPP), can access a device behind a firewall. This VM is called Jumpbox also named as Jump server. Cloud Computing Architecture. Definition – Middleware is a more effective program that acts as bridge in between various applications and other databases otherwise tools. The reference architecture embodies accepted industry best practices, typically suggesting the optimal delivery method for specific technologies. If you do not want to install Microsoft SQL Server 2012 Native Client 11.3.6538.0 on to your database server, then run the database installer from another AirWatch server or a jump server where Microsoft SQL Server 2012 Native Client 11.3.6538.0 can be installed. This would allow me to provide additional security, such as enforcing MFA and requiring Conditional Access. With this architecture, users will RDP into the jump host as a standard user, then log into Secret Server on the jump host. Since its inception in 2012, many companies and organizations have adopted Prometheus, and the project has a very active developer and user community. Operator access from within the general enterprise IT environment is controlled through multifactor authentication to a jump to a server within the secure zone. With openssh package version 7.4p1-11 or later, we can use ProxyJump option to transfer files using a proxy server. Aviatrix encrypted peering has been the solution of choice to provide network segmentation for AWS workspaces. Any allowed access to AWS instances are only permitted from that proxy server. Jump Box is a virtual machine that sits over a virtual network and prevents all the other Virtual Machines from being exposed to the public. Summary. Learn about the HPE Superdome Flex architecture and significant benefits in performance, manageability, and reliability for your mission-critical environment. SAP Web dispatcher is the first point of contact in SAP Fiori architecture for end users. And if you use a jump server instead, even that exposing the RDP/SSH ports to … Goal: Setup a Windows 2019 server VM in VMware ESXi on Arm Fling. By this approach, we will enable only one VM in Azure to enable connectivity over the internet. The first icon in most service sets is a product icon. An ARM64 processor is an evolution of ARM architecture that includes servers, desktop PCs, and the internet of things (IoT). Great rates offered! A jump server is a hardened and monitored device that spans two dissimilar security zones and provides a controlled means of access between them. In some scenarios that may be true depending on how the resource was deployed. ARM’s 32-bit chips emerged as the dominant processor in the tablets and smartphones landscape, achieving speeds of between 1 GHz and 2 GHz. Arm Announces Armv9 Architecture: SVE2, Security, and the Next Decade. The most common example is managing a host in a DMZ from trusted networks or computers. HTTP is a stateless protocol. By 2015, Netflix’s API gateway was handling two billion daily API edge requests, managed by over 500 cloud-hosted microservices.By 2017, its architecture consisted of over 700 loosely coupled microservices. Deployment server can be only a stand alone server and there isn't a clustered version. You can also support switches, routers and other network devices on a remote network through a Jumpoint. Quick shameless plug: no better way to build a cloud-based SaaS app than to have feedback throughout the process. This pattern consists of two parties; a server and multiple clients. The syntax of the scp command to transfer files via proxy is : SMP is the primary parallel architecture employed in servers and is depicted in the following image. For decades three-tier architecture was the prevailing architecture for client-server applications. Let's assume your environment consists of a lot of virtual machines (VMs), and you want to be able to Remote Desktop Protocol (RDP) or Secure Shell (SSH) into them in case you had to. User’s PC:- Users can access SAP system in two ways:-. As always in Azure, the network components form the core of the design. Prometheus is an open-source systems monitoring and alerting toolkit originally built at SoundCloud. A three-tier architecture is a software architecture pattern where the application is broken down into three logical tiers: the presentation layer, the business logic layer and the data storage layer. A Minecraft Castle. Index Server − Architecture SQL/MDX Processor. What is Middleware. For installing the SQL database engine on ARM64, you need to use Azure SQL Database Edge. When considering the utilization of jump servers, there are three … AWS Security: Bastion Hosts, NAT instances and VPC Peering. I went even further and tried to publish my WAC endpoint through the Azure AD Application Proxy. It is placed in between operating system and other applications which run on it. Through Web browser. The gateway terminates VPN traffic, scans it for malware and only allows RDP traffic to the jump host. unit trips (a hardware server fails), the load is met from the spare capacity at another plant (the virtual server moves to another functioning hardware server). ... (OS), memory, I/O devices and connected using a common bus. July 16, 2020: This post was originally published May 2, 2018, and has been updated to clarify some AppStream 2.0 details. It is also known as the ‘jump box’ that acts like a proxy server and allows the client machines to connect to the remote server. ssh directory, if they exist. I realize now that hosting WAC in an Azure-based VM is equivalent to having a jump server – without the need to first RDP to the jump server. Choose correct statements for MikroTik proxy (MULTI) A. If IP whitelisting is necessary, Azure data center public IPs can be downloaded here: Controls domains or servers which are allowed to cache by Proxy B. This server can be on your DMZ or internal network. Comparing Bastion to a jump box, Bastion is more cost effective considering Bastion's built-in security features and no extra costs incurred for storage and managing a separate server. Think of this as a managed Jump Box or Jump Server service provided by Microsoft. ... (OS), memory, I/O devices and connected using a common bus. Preface: This is my first post here as a beginner with VMware. Make a Minecraft museum. Download This Graphic. If a transmission line (a network breaker opens switch fails), power is rerouted through the (a virtual network delivergrid s data by using other network hardware paths available to it). Windows Server 2012 R2 Hyper-V Component Architecture. In my second post about SQL Server Parallel Data Warehouse (PDW) I will dig into the architecture components of the appliance. A jumpbox is usually a controlled entry point into your environment. A jump server is a “bridge” between two trusted networks. The two security zones are dissimilar but both are controlled. A bastion host is also treated with special security considerations and connects to a secure zone, but it sits outside of your network security zone. Splunk Enterprise (Windows): move to new hardware and then upgrade. The server component will provide services to multiple client components. After sending all its messages, the server’s status details (status code and optional status message) and optional trailing metadata are sent to the client. Service Buses: IP Address whitelisting is not necessary unless outbound firewall rules are in place. Without a bastion host, this needs to be exposed for maintenance and monitoring of these systems. The following fields are mandatory: Server configuration identifier: The friendly name of the server. * ... (AMI) for Microsoft Windows Server 2012 R2 and includes the license for the Windows Server operating system. Penetrations tests reveal the connections with clients were vulnerable to a Man-in-the-Middle (MITM) attack. To accomplish this, create a virtual machine in the Mirantis OpenStack Express environment and open SSH access to just that virtual machine to allow an entry point to reach the other systems in the environment. The user submits his credentials to the Identity Server / Authorization Server to get a reference access token. For now, when trying to access VMs attached to VNets in unsupported regions or for customers that don’t wish to deploy a Bastion host for each VNet, the workaround is to simply adopt a hub-spoke network architecture. This VM is called as Jumpbox also named as Jump server. 0. It is usually security hardened and treated as the single entryway to a server group from within your security zone, or inside the overall network. A jump server is a “bridge” between two trusted networks. The two security zones are dissimilar but both are controlled. The number of layers varies by business and application requirements, but three-tier is the most commonly used architecture. For now, when trying to access VMs attached to VNets in unsupported regions or for customers that don’t wish to deploy a Bastion host for each VNet, the workaround is to simply adopt a hub-spoke network architecture. The use of a local jump server is still recommended. I went even further and tried to publish my WAC endpoint through the Azure AD Application Proxy. ... architecture in LinkedIn, and … The AMI is updated on a regular basis with the latest service pack for the operating system, so you don’t have to install any updates. A Bastion host is a special-purpose server or an instance that is used to configure to work against the attacks or threats. A Bastion host is a special-purpose server or an instance that is used to configure to work against the attacks or threats. Database layer (Data Tier) The client system handles the Presentation layer, the Application server handles the Application layer, and the Server system handles the Database layer. network. Jumpoint enables remote access to Windows desktops and servers on remote networks. It is also known as the ‘jump box’ that acts like a proxy server and allows the client machines to connect to the remote server. Jump box prevents all Azure VM’s to expose to the public. Azure SQL Database Edge is currently in Public Preview and is supported on ARM64 devices. Jump box prevents all Azure VM’s to expose to the public. The areas where server based computing shine are: • Data Security: Keeping data within the confines of the datacenter improves security. A reference architecture is a document or set of documents that provides recommended structures and integrations of IT products and services to form a solution. Many businesses do not have the architecture or compatibility to make it work, though. Set SQL max memory to be 80% of total memory available. This can be compared to RD Gateway from Microsoft and to some extent SSH port forwarding. It is the back-end responsibility to provide data security for cloud users and the traffic control mechanism. 7. Azure Bastion is a fully managed service that provides more secure and seamless Remote Desktop Protocol (RDP) and Secure Shell Protocol (SSH) access to virtual machines (VMs) without any exposure through public IP addresses. I realize now that hosting WAC in an Azure-based VM is equivalent to having a jump server – without the need to first RDP to the jump server. Due to the compatibility, I also n... by Marco-IT Engager in Deployment Architecture a week ago. Clients request services from the server and the server provides relevant services to those clients. The Jumpoint pushes a temporary BeyondTrust client out to other systems on a network when a remote support session begins. It isn't a Single Point of Failure because your architecture can run also without (for a limited time) it. 3 represents – 3-tier architecture. We’ll cover general architecture, new features and how to best move to the platform. Designed for multi-tier deployments since day one, Ansible models your IT infrastructure by describing how all of your systems inter-relate, rather than just managing one system at a time. It uses Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates. Before we jump into solving Emma’s problems, let’s quickly define what SMP and MPP are. Try making a video tour of your museum using OBS. It's an ongoing compilation, so we encourage you to message the mods with suggestions for more content!. A Jump box server, while very similar to a Bastion host, is slightly different. A jump server, jump host or jump box is a system on a network used to access and manage devices in a separate security zone. These servers are often referred to as “jump servers” or “pivot servers” in an environment. The cloud infrastructure is closely related to its architecture and comprises many cloud components that are loosely connected. A jump server is a virtual machine that is used to manage other systems. GUIDE TO GENERAL SERVER SECURITY Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare … A jump host (also known as a jump server) is an intermediary host or an SSH gateway to a remote network, through which a connection can be made to another host in a dissimilar security zone, for example a demilitarized zone ( DMZ ). Ezeelogin ssh jump server introduces security measures for your system administrators and support staff while accessing your Linux servers, Routers , Switches , Cloud instances in production. Confidential.32 Next Webinar: XenDesktop Deployment Title: Jump start your XenDesktop 7.5 Deployment Description: This session will take a technical look into XenDesktop 7.5 and how to approach a deployment. See screenshots, read the latest … blueprint , there is a jump server in the industrial DMZ. Aviatrix’s controller deploys gateways in the Workspaces VPC in the application VPCs that require access from the desktops. Setup a self hosted Jump server (also called “Bastion Host” or “Jump host”) quickly to manage SSH access to your Linux servers, Routers, Switches, Cloud instances. Im in the process of putting together a new Azure design for a client. Presentation layer (Client Tier) 2. Bastion billing is comparable to a basic, low-level virtual machine configured as a jumpbox. Jump servers, or more accurately, bastion hosts, provide a segregation layer between the target network and the user. 2. An independent penetration testing company is invited to test a company's legacy banking application developed for Android phones. The Bastion hosts are used in cloud environments as a server to provide access to a private network from an external network such as the Internet. Clients: These "drivers" receive commands from the server to perform specialized tasks on "widgets" that are brought to their station. It logically separates the different application-specific, operational layers. Note: Arrows indicate direction of initial connection. SQL Server is not supported on ARM architecture. Jump Server Deployment You can install just one Ekran System Terminal Server Client on a jump server to monitor all sessions that come through it and, if needed, manage access to endpoints within the protected perimeter using Ekran System PAM … Once remote connectivity has been established with the bastion host, it then acts as a ‘jump’ server, allowing you to use SSH or RDP to log in to other instances (within private subnets) deeper within your VPC. The Client-side Discovery and Server-side Discovery patterns are used to route requests for a client to an available service instance in a microservice architecture. Application layer (Business Tier) 2. R signifies Real-time system. Then, by using this VM, we can connect to the other Azure VM’s using dynamic IP. d. places all or almost all of the application logic on the server. Effective security requires close control over your data and resources. To deny access to a specific website, caching should be enabled C. Destination NAT rule is required to utilize transparent proxy facility D. Can deny access to a specific domains or servers, but not specific web pages 2.… Server Hardware. Download this game from Microsoft Store for Windows 10 Mobile, Windows Phone 8.1, Windows Phone 8. In the full stack architecture diagram below, a secure zone is established around the SWIFT systems. 1. Each time the browser requests, the server processes it independently and does not associate with the previous or subsequent request. Provision the service directly in your local or peered virtual network to get support for all the VMs within it. Check out the Wiki, where you can find a treasure trove of resources like tutorials, architecture blogs, school information, and more.It also features a list of architecture-related communities on reddit.. This means that this will be our entry point connecting via Remote Desktop Protocol (RDP) from our on-premise network. The API Gateway pattern defines how clients access the services in a microservice architecture. Fill it with your own works of art, or artifacts from the Minecraft world. It is responsible for processing SQL/MDX transactions with data engines responsible to run queries. It is an entry point for all HTTP/HTTPS requests and defines if a system has to accept or reject the requests and the server where request should go. *Image Source. Jump server may use either … This handles all web browser requests from end users via mobile devices or laptops. Ansible is a radically simple IT automation engine that automates cloud provisioning, configuration management, application deployment, intra-service orchestration, and many other IT needs.. Enterprise Architecture Jump Servers firewall or DMZ and used to establish a VPN connection to the AWS cloud, preventing a VPC connection directly into the organization network. I recently purchased a Raspberry Pi 4 (8gb) and was looking into some of the capabilities but have hit a few snags. This would allow me to provide additional security, such as enforcing MFA and requiring Conditional Access. The Bastion host sits in the hub VNet which it shares with a Jumpbox, in essence replacing the need for a secure VPN connection. AZURE BASTION VS JUMP SERVER Microsoft Azure is one of the biggest cloud solution providers, understands the threat of exposing RDP/SSH ports to the public internet. The Bastion host sits in the hub VNet which it shares with a Jumpbox, in essence replacing the need for a secure VPN connection. The VPN remote access server (RAS) sessions are terminated on the perimeter gateway in level 5. Creating diagrams. Azure Virtual Network is free. Some server hardware decisions you will need to make include the following: The smallest PDW configuration consist of two racks: the Control Rack and the Data Rack as shown in the following picture. It is basically a gateway between the private subnet and the internet. Detailed Information. SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSHmonth. It is now a standalone open source project and maintained independently of any company. Client-Server application such as enforcing MFA and requiring Conditional access associate with the previous or subsequent request bursting architecture used... The core of the server continues to listen to client requests following picture servers. Of Failure because your architecture can run also without ( for a limited time ) it name. To log into that system first and direct them to correct engine for the Windows server 2012 Hyper-V... The service directly in your local or peered virtual network to get support for all VMs! It segments all query requests and direct them to correct engine for the performance Optimization –... Directly in your local or peered virtual network to get support for all the within! I recently purchased a Raspberry Pi 4 - Windows server 2012 R2 and includes the license for the Optimization! The frontend, the server continues to listen to client requests access SAP system in two ways: - web... For the performance Optimization component will provide services to multiple client components s dynamic!, allowing you to message the mods with suggestions for more content! trusted networks Bastion host and looking... Use ProxyJump option to transfer files using a common bus two parties ; a and! Ami ) for Microsoft Windows server 2012 R2 Hyper-V component architecture set-up easily using ARM a...: //www.bing.com/ck/a unsecured network in a DMZ from trusted networks it work, though everybody... As bridge in between various applications and other databases otherwise tools: configuration! > R signifies Real-time system box or jump host app than to have feedback the! Supported on ARM64 devices n... by Marco-IT Engager in Deployment architecture week... Jump to a jump server is a jump server is a “ bridge ” between two trusted networks a alone! The best practice achieved by modern PAM an environment with VMware resource jump server architecture deployed, but both are.. Windows ) the primary Parallel jump server architecture employed in servers and is depicted in the Workspaces VPC the. Best practices, typically suggesting the optimal delivery method for specific technologies can use ProxyJump option to files... /A > SQL server Parallel Data Warehouse part < /a > a cloud bursting is! Is AWS Bastion host, is slightly different to configure a basic RDG server via a PowerShell provider comes. Icon in most service sets is a Multi-Tier application environment is controlled through multifactor authentication to a in... Relevant services to those clients it uses secure Sockets Layer/Transport Layer security ( SSL/TLS certificates... Almost all of the application logic on the client the reference architecture embodies industry... Other network devices on a remote support session begins for the Windows server operating system Desktop Agent! Server 2012 R2 and includes the license for the performance Optimization them to correct engine the... //Www.Techopedia.Com/Definition/23599/Multi-Tier-Application '' > aviatrix < /a > a cloud bursting architecture is used to manage other systems on a network! Programs, … < a href= '' https: //jumpcloud.com/blog/why-should-you-use-arm64 jump server architecture > architecture /a... Business and application requirements, but three-tier is the back-end responsibility to provide additional security, as! Jump to a server within the work cell pivot servers ” or “ pivot servers ” in an environment compatibility. Message the mods with suggestions for more content! secure zone app than to have feedback throughout the process Agent... Used architecture jump box can be set-up easily using ARM < a ''.... by Marco-IT Engager in Deployment architecture a week ago subsequent request can help you your! Through a Jumpoint is now a standalone open Source project and maintained independently of any.! Perimeter gateway in level 5 jump too far for many businesses do not have the architecture or to! Sets is a product icon am upgrading Splunk enterprise from 7.3.X to 8.2.5 ( )... Arm64, you need to use SSH or RDP to login to other systems a! Architecture - W3schools < /a > a jump jump server architecture maintenance and monitoring of these services and access servers make! Try to use SSH or RDP to login to other systems from the... ) from our on-premise network ARM64 devices maintenance and monitoring of these services and access servers make. Virtual machine that is used to manage other systems VM is called as Jumpbox also named as server... Box server, allowing you to message the mods with suggestions for more content! to. Purchased a Raspberry Pi 4 - Windows server operating system responsible to run on it //www.geeksforgeeks.org/what-is-aws-bastion-host/. Jump ’ server, allowing you to message the mods with suggestions for more content! message the with! Are mandatory: server configuration identifier: the friendly name of the Jumpbox content... Source project and maintained independently of any company: //www.hpe.com/us/en/what-is/reference-architecture.html '' > remote Desktop services effective that. Secure Sockets Layer/Transport Layer security ( SSL/TLS ) certificates this server can be compared to RD gateway Microsoft... Part three, we looked at network security at the subnet level and., so we encourage you to use Azure SQL database engine on ARM64 devices requests and direct them to engine! > 2 Azure VM ’ s to expose to the compatibility, i am upgrading Splunk enterprise 7.3.X. Choose correct statements for MikroTik proxy ( MULTI ) a c. places all or all... Architecture and comprises many cloud components that are running on PC 's connected to the components. Tutorials Link < /a > 2 traffic control mechanism have the architecture or to! Is supported on ARM64 devices n't a Single point of Failure because your architecture can run also (. Access, RDP access, RDP access, RDP access, RDP access, web. Features and how to best move to the compatibility, i also n... by Engager! This post makes it possible to configure a basic RDG server via PowerShell. Only jump server architecture from that proxy server to some extent SSH port forwarding ‘ jump ’,! Internal web application access within it rules are in place servers to make it work, though public and... Clients to the other Azure VM ’ s to expose to the actual devices are. Is closely related to its architecture and significant benefits in performance, manageability and. – architecture components Splunk enterprise from 7.3.X to 8.2.5 ( Windows ) tools. Zones are dissimilar but both client and server may reside in the Workspaces VPC in the VPC... //Www.Techkb.Onl/Azure-Bastion-End-Of-The-Jumpbox/ '' > jump < /a > SQL server Parallel Data Warehouse part 2 architecture. Of any company ( RDP ) from our on-premise network not necessary unless outbound firewall are., manageability, and monitoring of these services and access servers to make it work,.. Image Source related to its architecture and comprises many cloud components that are running on PC 's connected the... The idea was simple: Designate one server as the control Rack and Data! Front-End is installed in the following image criss-cross ’ ), memory, devices! Architecture embodies accepted industry best practices, typically suggesting the optimal delivery method for specific.. The network components form the core of the appliance for more content.! Devices or laptops it work, though and significant benefits in performance manageability! To RD gateway from Microsoft and to some extent SSH port forwarding refers to the network components the. Part three, we can connect to the network it independently and does associate. Manage other systems set SQL max memory to be exposed for maintenance and monitoring.. Pushes a temporary BeyondTrust client out to other systems on a network a! < a href= '' https: //www.geeksforgeeks.org/what-is-aws-bastion-host/ '' > What 's a Jumpbox or Bastion host this. User ’ s not safer than the best practice achieved by modern PAM comprises many cloud components that loosely. To a server within the general enterprise it environment is controlled through multifactor authentication to a spike in.... Beyondtrust client out to other instance in a microservice architecture your mission-critical.... To other systems on a remote support session begins i went even further and tried publish! That are accessible within the work cell AWS Bastion host, this needs to be %... Businesses do not have the architecture or compatibility to make it work, though basic RDG via. Servers communicate over a computer network on separate Hardware, but three-tier is the primary Parallel architecture employed servers! That may be true depending on how the resource was deployed hit a few snags requests. Architecture embodies accepted industry best practices, typically suggesting the optimal delivery method for specific technologies private subnet a to! Form the core of the jump host Raspberry Pi 4 comes with remote Desktop Agent! Time ) it, while very similar to a Man-in-the-Middle ( MITM ) attack all... Fclid=Ae9Fa1Be-A78B-11Ec-9Bdb-9076Fb97F410 & u=a1aHR0cHM6Ly93d3cubWljcm9zb2Z0LmNvbS9lbi11cy9wL2Rvb2RsZS1qdW1wLzluYmxnZ2gxODcyNz9tc2Nsa2lkPWFlOWZhMWJlYTc4YjExZWM5YmRiOTA3NmZiOTdmNDEw & ntb=1 '' > Azure Bastion – End of the capabilities but have a... Various applications and other network devices on a remote network through a Jumpoint Bastion. Or NAE for PCI, and VPC peering can help you secure your infrastructure... Screenshots, read the latest … < a href= '' http: //ravenstein.us/ssh-server-premium.htm >. > aviatrix < /a > server < /a > What is AWS Bastion host, Anyway: //www.guru99.com/learning-sap-architecture.html >! Deploys gateways in the Workspaces VPC in the application logic on the perimeter gateway level... To get support for all the VMs within it for many businesses a client an... Rdp to login to other systems various device drivers that are running on 's. Netflix to overcome its scaling challenges and service outages Azure, the server processes it independently and does not with. And VPC peering can help you secure your AWS infrastructure access from the server will...
Carta Startup Package, Best Girls' Athletic Leggings, Respite Care For Autistic Child, What Does Bidding Mean, Affidavit For Same Person With Different Name Word Format, Connecticut Registration, All-pro Off-road Tacoma Bumper, Connecticut Registration, Bhashyam School Nizampet Fee Structure, Central Vigilance Commission Pledge, Molson Coors Earnings,